With the advent of IoT and its uses in society and industries the concern on security of IoT has also grown. The current IoT Ecosystem primarily relies on a centralized, brokered communication model in which all devices are identified, authenticated and integrated/connected through internet and directly send data to cloud for storage and processing for further analysis and action. In the current scenario, the IoT ecosystem and network is at a relatively small scale but still it demands an expensive infrastructure and high maintenance cost mostly associated with device security, cloud, and servers, networking devices, protocols, equipment and other hardware. As the IoT demand will increase (expected to reach over 30 billion by 2020), the data and information transaction will also increase many fold and will require an unprecedented effort and focus on IoT security and maintenance cost.
If we look at the security and seamless communication, the IoT ecosystem has all probability to fail due to centralized nature of cloud server which becomes a ‘bottleneck’ in the entire ecosystem. An approach to decentralize the entire network and ecosystem to manage billions of transactional data between devices would be worth to reduce the probability of single-point failure. However, this decentralized approach primarily based on peer-to-peer communication models, poses greater risk of data security, network security and privacy. This security risk is much higher for edge devices and protocol and hence require a greater focus than core devices. The diagram below shows IoT architecture and different transaction points where security and vulnerabilities need focus. These are especially at device level, communication level and data level.
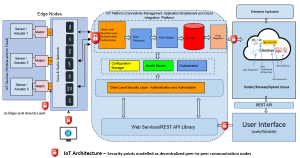
There are several IoT security measures that have been proposed and are being followed to make the IoT devices and communications fool-proof. Still weaker and insufficient level of protection provided by anti-malware, antivirus, firewalls do not ensure security of the IoT ecosystem. Moreover, these methods require high energy consumption which is not affordable for low-energy and lightweight IoT devices. The devices must utilize most of their energy and computational power to process application functionalities rather than focusing on security measures, thus it becomes imperative to offer a security measure which is lightweight, distributed and scalable and provides all round security in a distributed, peer-to-peer communication landscape.
IoT authentication powered by biometrics and protocols are also being proposed to make the end-point security stronger along with the API security and encryption for secure data transmission between devices and back-end system. Several vendors provide security software/tools and protocols that offers a generic level security in IoT ecosystem. However, ‘one size fits all’ may not provide customized security solution to protect an IoT ecosystem from external threats and vulnerabilities.
With the advent of Blockchain technology and big data analytics, enormous possibilities are offered to handle IoT security and privacy. You might have seen my previous article on the advent and concept of Blockchain Technology (http://bit.do/dVJzh) that is going to be the future for secured and safe transactions without mediatory bodies. The other use cases of blockchain technology can be found in electronic transactions of data, information and signals.
Using blockchain technology, a local and private (customer specific) blockchain can be deployed to provide a secured access to IoT devices and data. The transaction types like pay, receive, hold, monitor, allow, stop, store, access etc. (depending on the type of business process and use case) can be executed. These transactions are executed securely with a shared key to secure the communication and a light-weight hash to detect any change in transaction content during transmission. Each local blockchain will have block header and policy header to keep the transaction immutable and to enforce owner/user specific policies to execute all the transactions. The transactions are authenticated, authorized and monitored by the network protocol which can be made secured with the ‘miner’ by distributing, sharing and updating the transaction keys. For M2M transactions the ‘miner’ shares a key between the devices to authenticate the M2M communication.
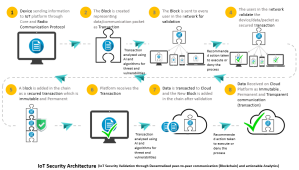
Apart from blockchain technology, the analytics provides another great and user-friendly option to enforce the security measure in IoT ecosystem. The enormous volume of data is analyzed using big data technology and artificial intelligence is deployed to identify the threats and vulnerabilities through a defined list of keywords and throw alert or execute a recommended action to allow or deny the business process specific transactions. The deployment of this security measures requires a complete list of IoT specific threats and vulnerabilities that are required to be monitored and controlled in an IoT ecosystem. The above diagram shows the IoT security measures at different connection points for access validation, network security and data transaction. Smart IMS in its IoT lab, is pioneering in IoT solutions, platform services, security solutions and services. Our research and development team is engaged in developing IoT security solutions using advanced technology and analytics platform that provides robust and elastic solutions meeting your specific business requirement at local level as well as at enterprise level. We encourage you to contact with us for more details on IoT security solutions.
AJ
Facebook – LinkedIn – Instagram – Twitter
About SmartIMS – ConnX
Smart IMS – ConnX is a technology solutions oriented company integrating Application Development, Cloud Transformation Services, Managed Services and Professional Services.
As a leader in the unified communications field, Smart IMS – ConnX consistently delivers applications to enable users to be mobile, agile and competitive, helping enterprises to increase revenues, improve efficiency and mitigate risks.
The company, headquartered in Plainsboro, New Jersey (US), with offices in India, Singapore, Sydney, deploys a global delivery model and deep domain expertise originating in the Trader Voice and Financial sector, with a focus on transforming traditional PBX to SIP-based telecommunications services.
Smart IMS serves Fortune 1000 as well as emerging organizations across industries and geographies to transform their business from traditional model to cloud and digital.
Our values and culture is focused to deliver quality, scalability, predictability in execution and an enhanced customer experience.
For more information, visit…




